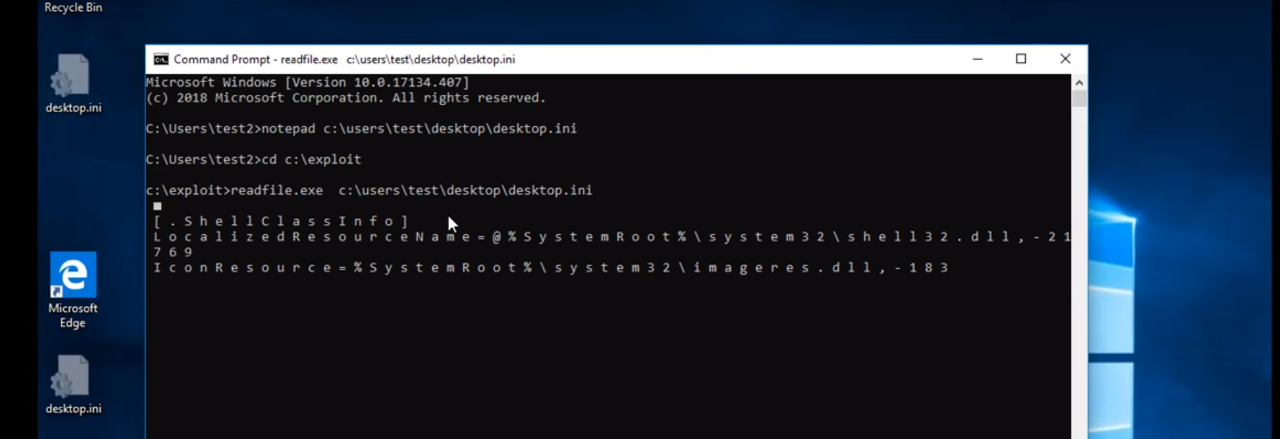
mariodevintoons on X: "I made this pico soul exe so do you like it KolSan https://t.co/6ecXYOobmR" / X

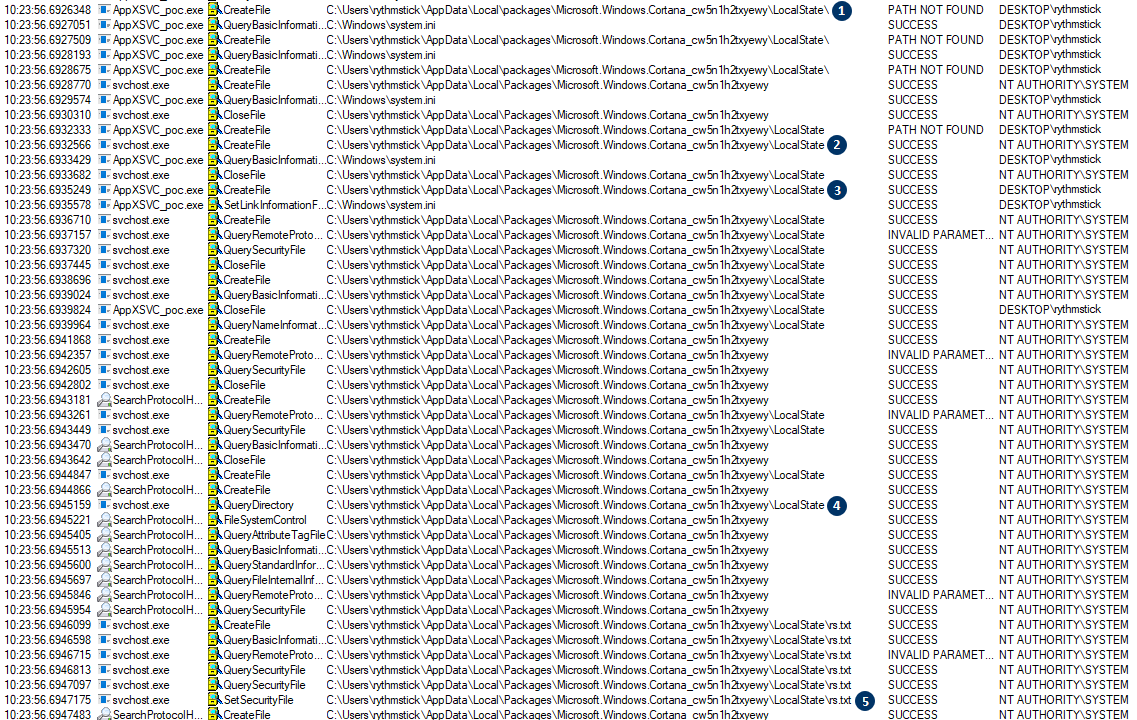
apppoolcreddecrypt: A POC to show how IIS App Pool credentials are decrypted without appcmd.exe - requires Administrator or SYSTEM privileges to run on the target : r/blueteamsec
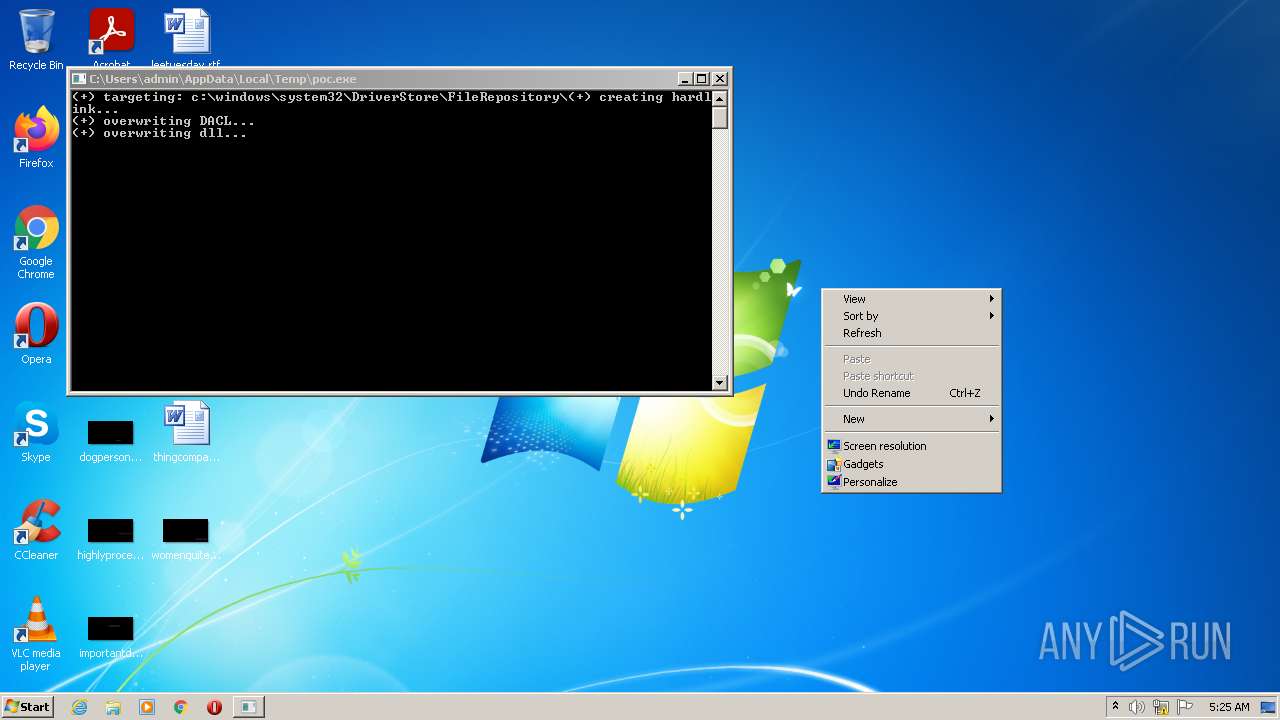
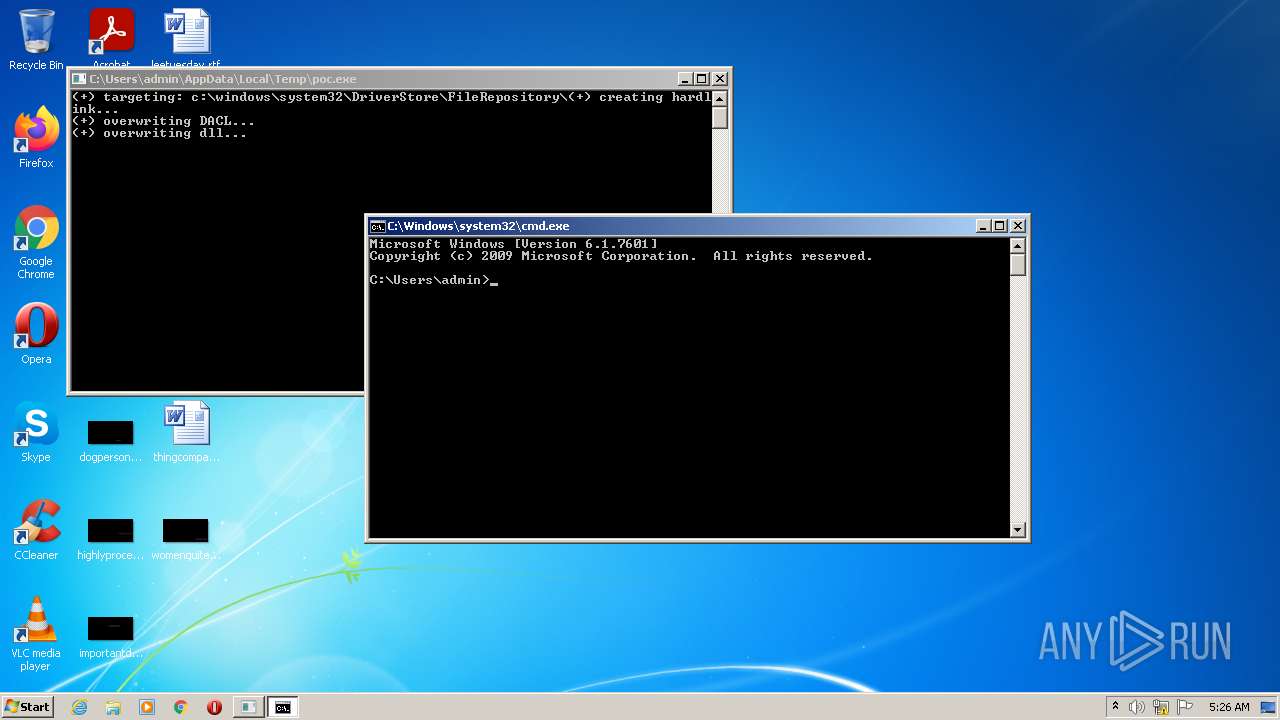
Creating Persistent Local Privilege Escalation with Temporarily Elevated Legitimate Installers - Atos

![pico.exe [Friday Night Funkin'] [Mods] pico.exe [Friday Night Funkin'] [Mods]](https://images.gamebanana.com/img/ss/mods/607224a1ec08a.jpg)




![FNF] Encore Pico.EXE (Requested) by 205tob on DeviantArt FNF] Encore Pico.EXE (Requested) by 205tob on DeviantArt](https://images-wixmp-ed30a86b8c4ca887773594c2.wixmp.com/f/06c35458-d939-41ba-9f21-97ddba28b8bd/dfjaz23-0b2d5c29-247b-46a5-b5e5-f01fbe5d21a3.png/v1/fill/w_382,h_466/_fnf__encore_pico_exe__requested__by_205tob_dfjaz23-fullview.png?token=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJ1cm46YXBwOjdlMGQxODg5ODIyNjQzNzNhNWYwZDQxNWVhMGQyNmUwIiwiaXNzIjoidXJuOmFwcDo3ZTBkMTg4OTgyMjY0MzczYTVmMGQ0MTVlYTBkMjZlMCIsIm9iaiI6W1t7ImhlaWdodCI6Ijw9NDY2IiwicGF0aCI6IlwvZlwvMDZjMzU0NTgtZDkzOS00MWJhLTlmMjEtOTdkZGJhMjhiOGJkXC9kZmphejIzLTBiMmQ1YzI5LTI0N2ItNDZhNS1iNWU1LWYwMWZiZTVkMjFhMy5wbmciLCJ3aWR0aCI6Ijw9MzgyIn1dXSwiYXVkIjpbInVybjpzZXJ2aWNlOmltYWdlLm9wZXJhdGlvbnMiXX0.QnxmFTEBOw6OmSvLy3GguA6WaL_zJs6qexxQAJ5cD6w)